先来看看这个函数的
BOOL
WINAPI
DebugActiveProcess(IN DWORD dwProcessId)
{
NTSTATUS Status, Status1;
HANDLE Handle;
/* Connect to the debugger */
Status = DbgUiConnectToDbg();
if (!NT_SUCCESS(Status))
{
BaseSetLastNTError(Status);
return FALSE;
}
/* Get the process handle */
Handle = ProcessIdToHandle(dwProcessId);
if (!Handle) return FALSE;
/* Now debug the process */
Status = DbgUiDebugActiveProcess(Handle);
/* Close the handle since we're done */
Status1 = NtClose(Handle);
ASSERT(NT_SUCCESS(Status1));
/* Check if debugging worked */
if (!NT_SUCCESS(Status))
{
/* Fail */
BaseSetLastNTError(Status);
return FALSE;
}
/* Success */
return TRUE;
}DebugActiveProcess内部调用DbgUiDebugActiveProcess
NTSTATUS
NTAPI
DbgUiDebugActiveProcess(IN HANDLE Process)
{
NTSTATUS Status;
/* Tell the kernel to start debugging */
Status = NtDebugActiveProcess(Process, NtCurrentTeb()->DbgSsReserved[1]);
if (NT_SUCCESS(Status))
{
/* Now break-in the process */
Status = DbgUiIssueRemoteBreakin(Process);
if (!NT_SUCCESS(Status))
{
/* We couldn't break-in, cancel debugging */
DbgUiStopDebugging(Process);
}
}
/* Return status */
return Status;
}DbgUiIssueRemoteBreakin调试器附加断点的关键函数
先来看看内部
NTSTATUS
NTAPI
DbgUiIssueRemoteBreakin(IN HANDLE Process)
{
HANDLE hThread;
CLIENT_ID ClientId;
NTSTATUS Status;
/* Create the thread that will do the breakin */
Status = RtlCreateUserThread(Process,
NULL,
FALSE,
0,
0,
PAGE_SIZE,
(PVOID)DbgUiRemoteBreakin,
NULL,
&hThread,
&ClientId);
/* Close the handle on success */
if(NT_SUCCESS(Status)) NtClose(hThread);
/* Return status */
return Status;
}它会创建一个远程线程到调试的进程里
线程的地址为DbgUiRemoteBreakin
VOID
NTAPI
DbgUiRemoteBreakin(VOID)
{
/* Make sure a debugger is enabled; if so, breakpoint */
if (NtCurrentPeb()->BeingDebugged) DbgBreakPoint();
/* Exit the thread */
RtlExitUserThread(STATUS_SUCCESS);
}也就是说 线程会运行在这个函数的地址 至于为什么会断下 是因为
DbgBreakPoint()看完了附加创建线程后,来看看插件是怎么处理这个Flag的
如:StrongOD HOOK
LdrInitializeThunk 跳转到自身申请的内存 并且内联汇编制造断点以及退出 从而避免走DbgUiRemoteBreakin这个函数VOID
NTAPI
LdrInitializeThunk(ULONG Unknown1, // FIXME: Parameters!
ULONG Unknown2,
ULONG Unknown3,
ULONG Unknown4)
{
UNIMPLEMENTED;
return;
}RtlUserThreadStart-LdrInitializeThunk
自此 我们就有了对抗的方法
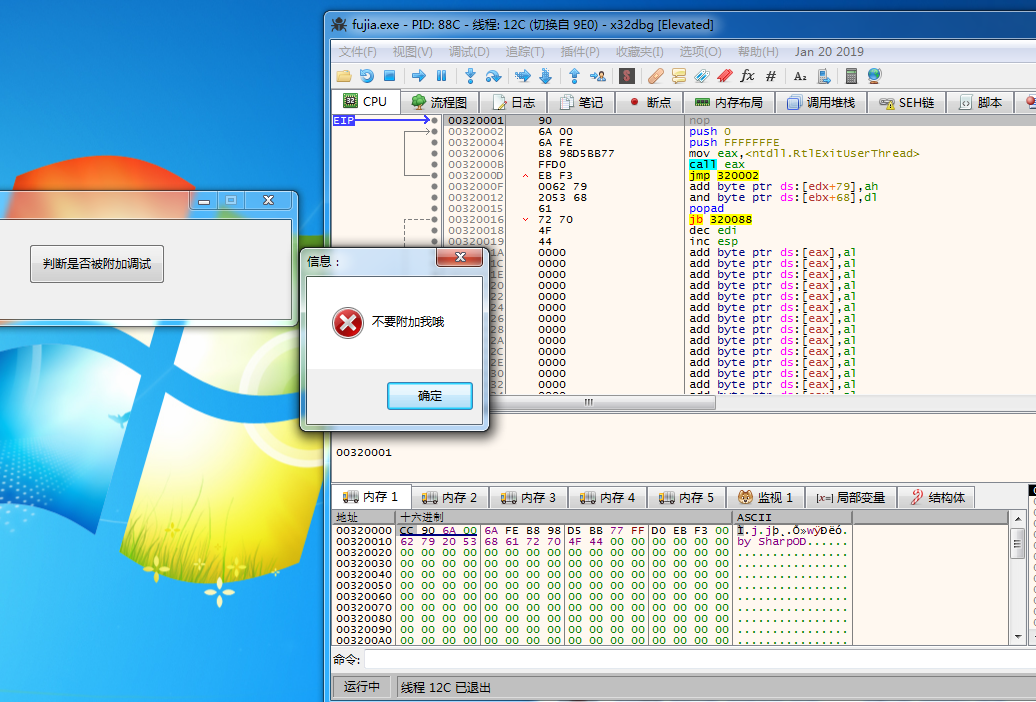
x64dbg Sharpod AntiAntiAttach
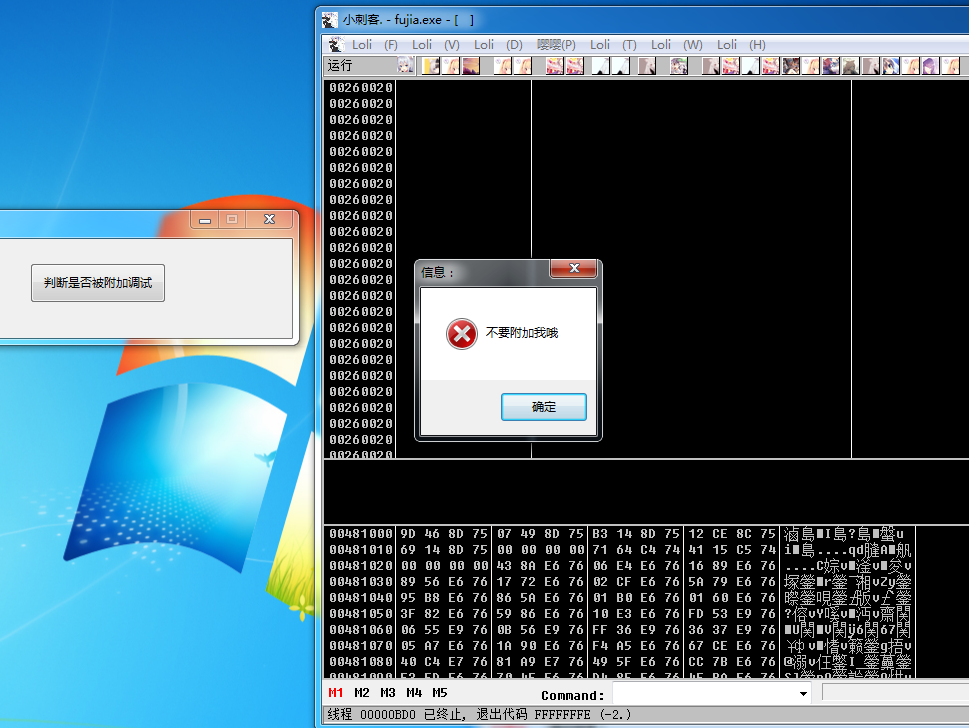
ollydbg Strongod AntiAntiAttach
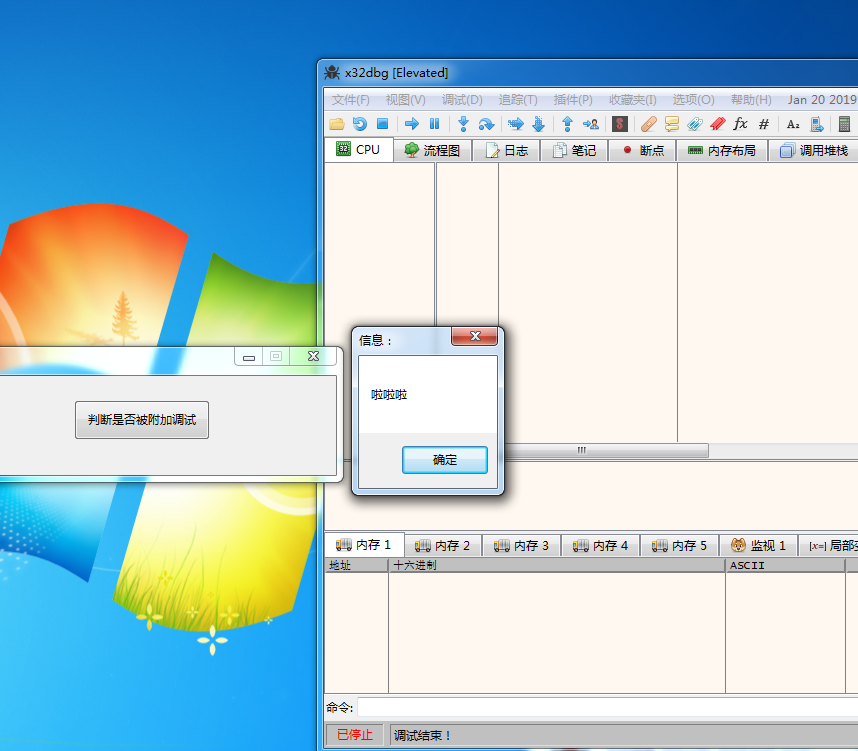
正常运行
